Our team of experts provides consulting and outsourcing services in Security Management, addressing the following fields: public services and Government, Public Safety, Environment, Agriculture, Transport, Healthcare, Energy and Utilities. With our help, the companies may increase their IT security level, both by implementing new security policies and processes, enabling them to receive the certification for ISO 27001/PCI Information Security Standard and by expanding the capacity of their own IT teams while using our outsourcing services.
- Penetration Tests
- Risk Management
- Information Security Programmes
- Training of users
- Incident Management
- Disaster Recovery and Business Continuity Management
- Compliance with the Legislation
The IT Security Consulting Services are designed to provide the support required in order to get an ISO 27001 / PCI certification – Information Security Standard, to build up information security policies and processes at company level, which are alligned with the current best practices in the industry, to develop data-leak prevention strategies, as well as to create and implement secured applications.
- Administration of Prevention/ Detection Systems (IDS/IPS)
- Firewall Adminstration
- Web Traffic Filtering
- Data-Leak Prevention (DLP)
- Log Monitoring/Retention
- Monitoring 24/7
- Vulnerability Management
- Web Applications Firewall
- Web Applications Securization
- Incident Management
- Security Policies Management
- Mobile Devices Encryption
Our Security Management Services expand the capacities of the IT and Security team of the Client, adding value to our specialists’ expertise who work on improving the security level in order to cut down the risks and to boost the efficiency of IT security.
AThENA (Advanced THreat and Event aNomaly Alerting)
Event management and security information market is defined by organizations’ needs to apply Real Time Data and System Security Measures, to detect security breaches early, to collect and aggregate data and to report on log files. All these can be used in internal investigations or compliance audits.
Evolution security challenges
- Cyberspace Environment has become increasingly more complex by the fact that users are becoming increasingly mobile and more services are published to the Internet or in the cloud, thus growing diversity and number of sources of data to be analyzed;
- The number of attacks that are going to establish a bridgehead in the organization persistently have increased, also on the increasing number of platforms connected to resources,
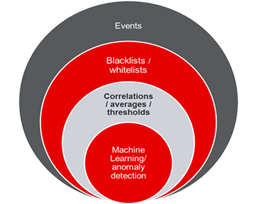
- Most current monitoring solutions uses static models such limits, blacklists / whitelists, etc.
A new approach is needed to keep up with the significantly increase if the number of security devices. Therefore, we present a new product developed by our team, AThENA.
AThENA overview
Leveraging Open Source technologies like NoSQL, Stream Processing and Hadoop we have successfully build a Big Data Security Analytics system that combines data from multiple sources and does complex, real-time correlations between all of them.
All components that were used are highly clustered for both high performance and high availability, enabling the use of commodity hardware.
The Big Data Security Analytics creates a platform where detection is not based on signatures or static correlation rules but on dynamic comparisons to normal baseline behaviors for individuals or groups. Behavior outside the normal baseline determines suspicious activities that may indicate attacker activity.
Specifications
Roles
- Event Receiver
- Event Parser
- Event Aggregation/ Correlation
- Machine Learning for anomaly detection
Data Collection
- Syslog
- Real-time file tailing
- Database query
- Agent base collection
- PCAP Capture
Platform Modules
The core system provides the following basic functionalities:
- Event Collection from Network devices, Operating Systems and applications (machine exhaust);
- Event Repository in a high performance and availability database;
- Creating Analyses and Building Dashboards;
- Creating and managing custom alerts
The following functionalities can be added to the core system:
- Real-Time Event Correlation between multiple data sources, which can process hundreds of thousands of events per second per processing node;
- Packet Analysis at the Network layer;
- Machine Learning for anomaly detection is also available in order to augment already preprocessed results;
- Event Collection, Interpretation, Correlation and Alerting based on operating system metrics and application through the use of logged information.
- CISSP – Certified Information Systems Security Professional
- CISM – Certified Information Security Manager
- CISCO Certified Specialist
- FortiNet Certified Specialist
- CEH – Certified Ethical Hacker
- ECSA – EC-Council Certified Security Analyst
- CISA – Certified Information Systems Auditor
- CGEIT – Certified in the Governance of Enterprise IT
- HP Certified Technicians
- PMP – Project Management Professionals